Blockchain Glossary
The glossary, like blockchain, is a work in progress.
| A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
A
- Advanced Knowledge Architecture for Social Human Advocacy (AKASHA)
- AKASHA is a social and technological experiment enabling collective memory, feelings and ideas to echo freely throughout humanity’s existence. By fusing Ethereum with the Inter-Planetary File System (IPFS), it explores the implications and applications of a permanent Web in the context of freedom of expression, creative perpetuity, and privacy.
- Air Drop
- An airdrop generally refers to the widespread distribution of digital tokens to community members either for free or in exchange for performing menial tasks. Airdrop of tokens to third parties by means of a "bounty program" in exchange for online promotional and marketing services that target potential investors and direct them to the Company’s offering materials.
- Altcoin
- Coins other than major cryptocurrency coins like Bitcoin and Ethereum.
- Anti-Money Laundering (AML)
- Atomic Swaps
- Methods for enabling two parties to swap two cryptocurrencies directly across separate blockchains instantly and without interruption. Atomic swaps would enable a user-friendly method of decentralized exchange across a wide range of cryptocurrency ecosystems without relying on exchanges.
- Application Specific Integrated Circuit (ASIC)
- An ASIC (application-specific integrated circuit) is a microchip designed for a special application, such as a particular kind of transmission protocol or a hand-held computer. Custom blockchain ASICs are used to accelerate the speed and efficiency of Proof of Work mining.
- Arbitrator
- A human in a blockchain that is able to sign the transaction after some blockchain-based validation.
- Autonomous Decentralized Peer-to-Peer Telemetry (ADEPT)
- Blockchain-type technology to form the backbone of a decentralized network of IoT devices. IBM and Samsung are working with this approach. (As of February 2018)
B
- Big Data
- Extremely large and complex datasets analyzed computationally to reveal patterns, trends, and associations within the data. The term big data includes the capability to capture, store analyze, curate, search, share transfer, and visualize. Big data processes mine structured, semi-structured and unstructured artifacts to find and extract information.
- Bilateral | Multilateral Consensus
- Bilateral consensus mechanisms occur the two counterparties in a transaction validate the transaction themselves node-to-node without participation of others participating in the ledger unless the two counterparts permit it. Multilateral consensus involves multiple parties to a transaction participating in consensus decisions.
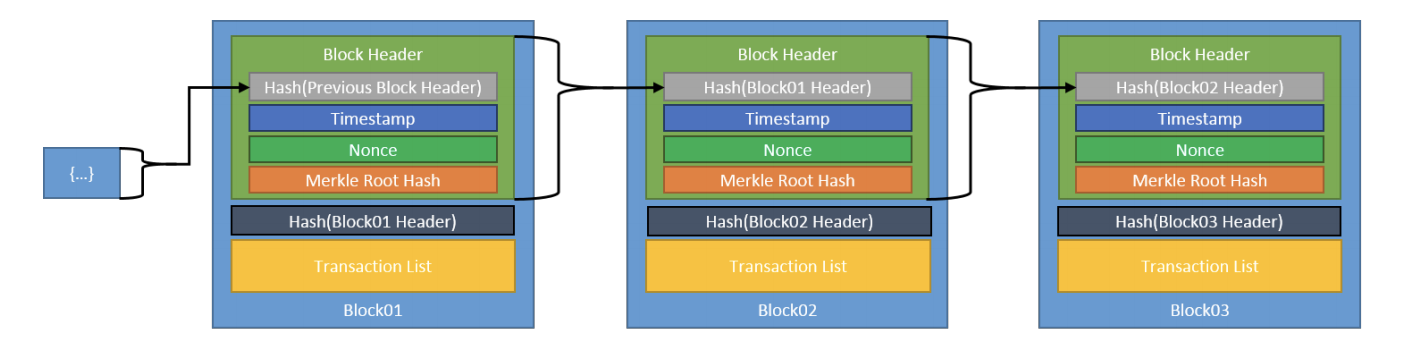
- Block
- A set of validated transactions.
- Block Header
- The portion of the block that contains information about the block itself (block metadata), usually including a timestamp for posting the block; the Merkle tree root hash; the previous block's hash, and the cryptographic nonce (if needed.)
- Block-less Data | Block-less Chains
- Writing transactions directly to the blockchain without assembling them into blocks.
- Block Signers
- The actors in a proof-of-stake blockchain that are responsible for validating transactions and adding them to the blockchain. (Source: IEEEE)
- Blockchain
- A distributed ledger of cryptographically signed transactions that are grouped into blocks. Each block is cryptographically linked to the previous block after validation and undergoing a consensus decision. As new blocks are added, older blocks are increasingly hard to modify. New blocks are replicated across all copies of the ledger within the blockchain/ledger network.
- Blockchain as a Service (BaaS)
- Blockchain platforms with a range of features to support faster design, development, and deployment of enterprise blockchain solutions. Microsoft offers its Ethereum and Azure-based enterprise blockchain platform as BaaS. IBM's Blockchain as a Service offering is built using Hyperledger, the IBM Cloud and IBM Bluemix for Edge-based and Internet of Things (IoT) capabilities.
- Blockchain Insurance Industry Initiative (B3i)
- B3i was formed to explore the potential of using Distributed Ledger Technologies within the re/insurance and commercial insurance industry for the benefit of all stakeholders in the value chain. B3i provides insurance solutions on a blockchain platform offering opportunities for efficiency, growth and quality across the value chain to benefit all participants including end customers.
- Blockchain in Supply Chain Alliance (BISCA)
- Blockchain in Supply Chain Alliance (BISCA) is an offshoot of the Blockchain in Transport Alliance (BITA). The new alliance will focus on planning, procurement, transportation and warehousing, with some overlap with BITA, whose members include prominent third party logistics (3PL) entities like UPS and FedEx. BISCA is focusing on four key pillars: 1) Procurement; 2) Planning; 3) Transportation; and, 4) Warehousing.
- Blockchain in Transport Alliance (BITA)
- BITA was formed by experienced technology and transportation executives to create a forum for the development of blockchain standards and education for the freight industry.
- Byzantine Fault Tolerant Proof of Stake Consensus Model
- A proof of stake consensus model where the blockchain decides the next block by allowing all stake members to "vote" on which submitted block to include next.
- Blockchain Offered New Debt Instrument (BONDI)
- Burning Tokens
- Burning tokens occurs when a token is destroyed when a user receives something of value. This differs from spending tokens where tokens are exchanged and still exist after the exchange is finished.
C
- Camenisch-Lysyanskaya Signature (CL)
- Signatures with efficient protocols are a form of digital signature invented by Jan Camenisch and Anna Lysyanskaya in 2001. In addition to being secure digital signatures, they need to allow for the efficient implementation of two protocols:
- A protocol for computing a digital signature in a secure two-party computation protocol.
- A protocol for proving knowledge of a digital signature in a zero-knowledge protocol.
- Casper
- Casper "the friendly ghost" because it is an adaptation of some of the principles of the GHOST (Greedy Heaviest-Observed Sub-Tree) protocol for proof-of-work consensus to proof-of-stake. Casper is a proof of stake consensus algorithm for blockchains. Casper is broadly a Byzantine fault tolerant (BFT) based proof of stake. Casper requires validators to vote and cryptographically sign their vote message before broadcasting it to all other validators. Proof of stake is intended as a long-term replacement for the proof of work (PoW) system that is currently used in Ethereum. Casper represents an intermediary step to keep using proof of work but also add proof of stake as an additional layer of finality.
- Chain-based Proof of Stake
- A proof of stake consensus model where the blockchain system decides the next block through pseudo-random selection based on a personal stake to overall system asset ratio.
- Coco Framework
- A permissioned version of Ethereum supported by Microsoft. The Azure cloud is used as the delivery platform for the Coco Ethereum-based blockchain technology. Unveiled in August 2017.
- Colored (Coloured) Coins
- The term "Colored Coins" loosely describes a class of methods for representing and managing real world assets on top of the Bitcoin blockchain.
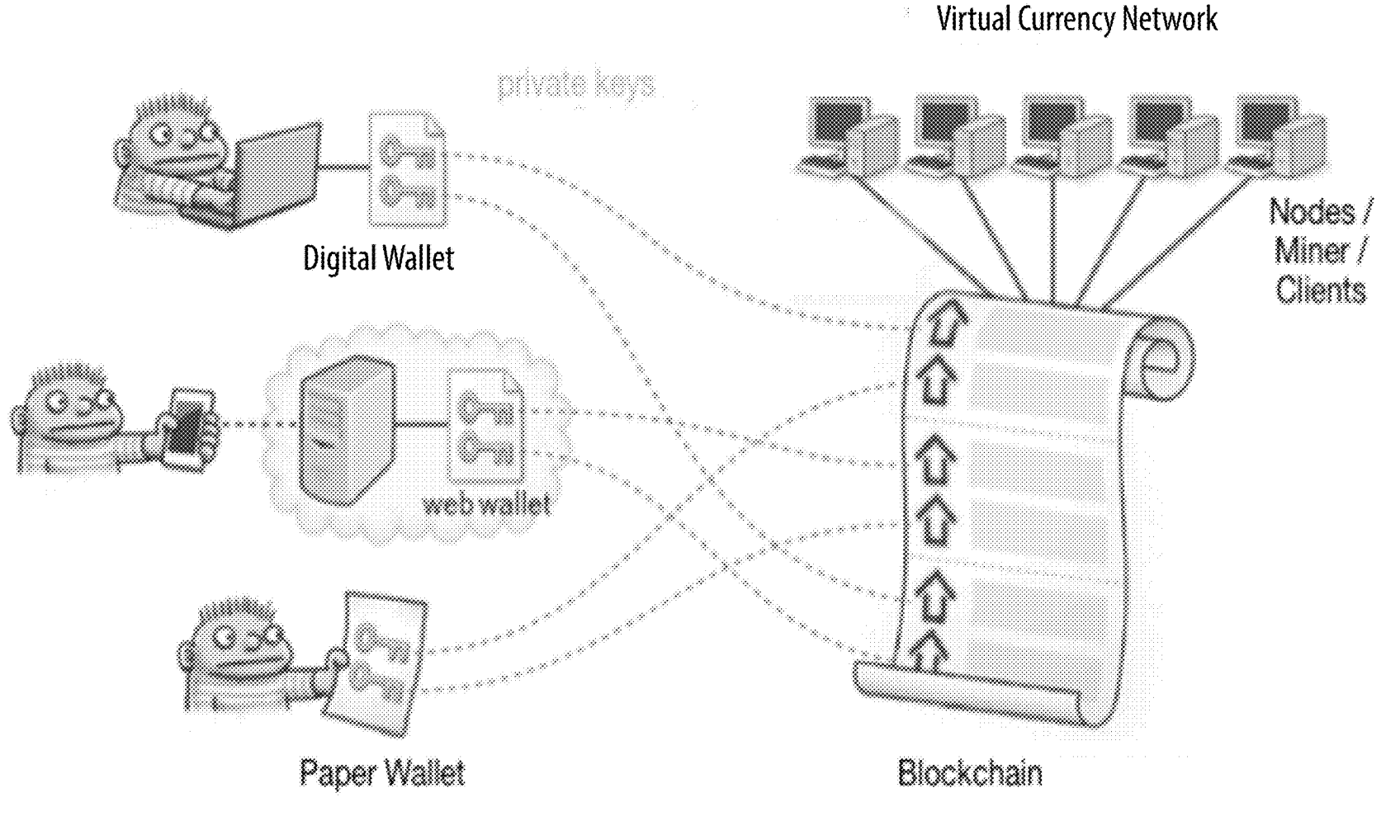
- Cold Wallet
- Cryptocurrency storage not connected to the internet. Cold wallets may be a hardware device or a paper wallet.
- Conflict
- One or more participants disagree on the state of the system.
- Conflict Resolution
- A predefined method for coming to a consensus on the state of the system (e.g. when portions of the system participants claim to be in one state and the rest of the participants are in a different state.) The conflict resolution mechanism automatically resolves the conflict by choosing the "valid" state as being the one from whichever group adds the next block of data; any transactions that are "lost" by the state not being selected are added back into the unspent transaction pool.
- Consensus
- A predefined method to determine whether some data can be committed to the data store of the blockchain. Also called Consensus Algorithm or Consensus Model.
- Consensys
- Consensys is a blockchain innovation lab focused on promoting Ethereum-based uses of blockchain technology.
- Consortium Blockchain
- A blockchain that supports a group of entities with specific business or operational requirements. Also referred to as a Federated Blockchain. Members of the consortia establish the rules that govern the operation of the consortia blockchain and make decisions about how consensus will be reached.
- Critical infrastructure
- Systems and assets, whether physical or virtual, that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic security, national public health safety, or any combination of those matters.
- Cryptocurrency
- A digital representation of value that is not issued or guaranteed by a central bank or a public authority, is not necessarily attached to a legally established currency and does not possess a legal status of currency or money, but is accepted by natural or legal persons as a means of exchange and which can be transferred, stored and traded electronically. Also called virtual currency.
- Cryptographic hash function
- A function that maps a bit string of arbitrary length to a fixed-length bit string. Hash functions satisfy the following properties:
- (One way) It is computationally infeasible to find any input that maps to any pre-specified output; and
- (Collision resistent) It is computationally infeasible to find any two distinct inputs that map to the same output.
- Crypto-Jacking
- A process where a victim unknowingly has software installed onto their browser to mine cryptocurrency on a hacker's behalf.
D
- authenticity — users can verify that the message was signed with a private key corresponding to a specific pubic key,
- non-repudiation — a user cannot deny having sent the message; and
- integrity — the message was not altered during transmission.
E
- Edge-computing model
- A computing model where data is processed where it is created rather than at a remote or cloud-based data center, minimizing costs by reducing network traffic and server usage. Edge computing is used to support many Internet of Things (IoT) devices and used in conjunction with blockchain supply chain systems. (Also referred to as Fog Computing)
- Energy Web Foundation (EWF)
- The Energy Web Foundation is a global non-profit organization focused on accelerating blockchain technology across the energy sector.
- Enterprise architecture
- A strategic information asset base, which defines the mission; the information necessary to perform the mission; the technologies necessary to perform the mission; and the transitional processes for implementing new technologies in response to changing mission needs. Enterprise architecture includes a baseline architecture; a target architecture; and a sequencing plan to move from one to the other.
- Enterprise Ethereum Alliance (EEA)
- The Enterprise Ethereum Alliance connects Fortune 500 enterprises, startups, academics, and technology vendors with Ethereum subject matter experts.
- Epoch
- In Proof of Stake (PoS) consensus blockchains an epoch is a period of time. Epochs are divided into block intervals (Ethereum Casper) or slots (Cardano).
- ERC-20
- ERC-20 defines a common list of rules for Ethereum-compliant tokens. This token standard enables developers of all types of dApps to accurately predict how new tokens will function within the larger Ethereum system. ERC stands for Ethereum Request for Comments.
- ERC-721
- ERC-721 is a free, open standard that describes how to build non-fungible or unique tokens on the Ethereum blockchain. While most tokens are fungible (every token is the same as every other token), ERC-721 tokens are all unique. ERC-721 defines a minimum interface a smart contract must implement to allow unique tokens to be managed, owned, and traded. It does not mandate a standard for token metadata or restrict adding supplemental functions. ERC-721 tokens are used for unique digital object like cryptokitties or for more mainstream functions like certifications for training.
- Ethereum
- Ethereum is an open-source, public, blockchain-based distributed computing platform featuring smart contract functionality, a distributed ledger for state transitions. It is the blockchain network for Ether (ETH), a cryptocurrency. Initial release: 30 July 2015.
- Ethereum Virtual Machine (EVM)
- The Ethereum Virtual Machine (EVM) is the runtime environment for smart contracts using Ethereum. Every Ethereum node runs the EVM in order to maintain consensus across the blockchain. Decentralized consensus gives Ethereum high levels of fault tolerance, ensures zero downtime, and makes data stored on the blockchain immutable and censorship-resistant. The code running inside the EVM has no access to network, file system, or other processes. Smart contracts running on the EVM have limited access to other smart contracts. Smart contracts are typically written in an Ethereum high level language, compiled into byte code using an EVM compiler, and uploaded on the blockchain using an Ethereum client.
F
- Fabric
- Fabric refers to Hyperledger Fabric. Hyperledger Fabric is a platform for distributed ledger solutions underpinned by a modular architecture delivering a high degree of confidentiality, resiliency, flexibility and scalability. It is designed to support pluggable implementations of different components and accommodate the complexity and intricacies that exist across the economic ecosystem.
- Fiat Currency
- The legal tender, usually paper currency, of a government. It implies centralized control of financial transactions by the banking system. Fiat currency, or fiat, is exchanged for cryptocurrency coins.
- Fifty One Percent Attack | 51% Attack
- 51% attack occurs when a group of blockchain users control the majority of the network's computing power and effectively determine the blockchain’s accuracy.
- Fork
- A change to blockchain software and implementation is called a fork. See also Hard fork and Soft Fork.
- Full Node
- A blockchain node that stores the blockchain data, passes along the data to other nodes, and ensures that newly added blocks are valid.
G
- Genesis Block
- The first block of a blockchain system; it records the initial state of the system.
- Geth
- Geth (Go Ethereum) is a multipurpose command line tool that runs a full Ethereum node implemented in the Go programming language. It offers three interfaces: 1) the command line subcommands and options; 2) a Json-rpc server; and 3) an interactive console. Geth is a program that serves as a node for the Ethereum blockchain, and through which a user can mine Ether (ETH) and create software which runs on the EVM – the Ethereum Virtual Machine.
H
- Hard Fork
- A hard fork prevent users who do not adopt it from using the changed blockchain. Users must either upgrade to stay with the developer's main fork or continue to use the original path without upgrades. Users on different hard forks cannot interact with one another.
- Hardware Wallet
- Hardware wallets are hardware devices build specifically for handling private keys and public addresses. It consists of a USB-like device with an OLED screen and side buttons to navigate through the interface of the wallet and comes with its native desktop apps for different cryptocurrencies. It is a battery-less device that connects to a PC or mobile device via USB port.
- Hash
- Hashing is the transformation of a string of characters into a usually shorter fixed-length value or key that represents the original string. A cryptographic hash function is a hash function which takes an input (or message) and returns a fixed-size alphanumeric string. The string is called the hash value, message digest, digital fingerprint, digest or checksum. The ideal hash function has three main properties:
- It is extremely easy to calculate a hash for any given data.
- It is extremely computationally difficult to calculate an alphanumeric text that has a given hash.
- It is extremely unlikely that two slightly different messages will have the same hash.
- Hash Chain
- A append-only data structure where data is bundled into blocks that include a hash of previous block's data within the newest block. This data structure provides evidence of tampering because any modification to a block's data will change the digest recorded by the following block.
- Hash Digest
- The output of a hash function — hash(data)=digest. Also known as a digest.
- Hash function
- An algorithm that ingests a chunk of data of arbitrary size and turns it into a string of numbers and letters of fixed length, called a hash.
- Hashing
- A method of calculating a relatively unique output (called a hash digest) for an input of nearly any size (a file, text, image, etc.) Hash algorithms are designed to be one-way; calculating the digest of an input is simple, but reconstructing the input from the digest is significantly difficult. Hashing needs to be collision-resistant, so that it is computationally infeasible to find two inputs which result in the same digest. The smallest change of input, even a single bit, will result in a completely different output digest.
- HODL — Hold On for Deal Life
- Cryptocurrency and blockchain enthusiasts who will never sell. Not a typo.
- HODLer
- People who are committed to the potential of blockchain.
- Hot Wallet
- A cryptocurrency wallet that is connected to the internet. Internet connected hot wallets are applications in the cloud, on desktop computers or on mobile devices.
- Howey Test
- The Howey Test is a test created by the Supreme Court for determining whether certain transactions qualify as "investment contracts." Howey Test, requires (1) an investment of money (2) in a common enterprise where (3) there was an expectation of profits to be derived solely from the efforts of others. If these transactions are determined to be transactions under the Howey Test, then under the Securities Act of 1933 and the Securities Exchange Act of 1934, those transactions are considered securities and therefore subject to certain disclosure and registration requirements. One of the important issues surrounding both cryptocurrency and ICO issued tokens is whether these digital assets are securities.
- Hybrid Ledger
- A hybrid ledger operates private and public transactions. Some transactions are highly permissioned and executed among parties with an offline relationship or exhibiting certain security-based characteristics to protect the confidentiality of the transactions but with additional public key distribution for some aspects of the supply chain to broaden and strengthen reliability of transaction credibility.
- Hyperledger
- Hyperledger is an open source collaborative effort created to advance cross-industry blockchain technologies. It is a global collaboration, hosted by The Linux Foundation, including leaders in finance, banking, Internet of Things, supply chains, manufacturing, and Technology.

I
- Immutability
- Unchanging over time or unable to be changed. A foundational principle in blockchain is that once transactions or information is recorded in a blockchain decentralized database it can't be changed.
- Information Security Architecture
- An embedded, integral part of the enterprise architecture that describes the structure and behavior of the enterprise security processes, information security systems, personnel, and organizational subunits, showing their alignment with the enterprise’s mission and strategic plans.
- Initial Coin Offering (ICO)
- An Initial coin offering is a way of funding new businesses and application development for business models and technology that will be deployed on blockchains. ICOs are predominantly associated with start-up ventures. During an ICO a firm sells its proprietary cryptocurrency tokens or utility coins that will be used to operate the application in the future. Purchasers of these tokens do not own equity in the company but instead own the coins that are expected to rise in value once the entity selling them becomes operational. ICO tokens have been deemed to be securities by US financial regulatory bodies because unlike Bitcoin and Ethereum these tokens are NOT decentralized. Also referred to as a Coin Offering.
- Internet of Things (IoT)
- Internet of Things refers to the network of physical devices, vehicles, home appliances and other items embedded with electronics, software, sensors, actuators, and connectivity which enables these things to connect and exchange data, creating opportunities for more direct integration of the physical world into computer-based systems, resulting in efficiency improvements, economic benefits and reduced human intervention. Blockchain and use of tokens for payment is perceived by some to be a major enabler of IoT-based applications and processes.
- Interplanetary File System (IPFS)
- Interplanetary File System is a protocol and network designed to create a content-addressable, peer-to-peer method of storing and sharing hypermedia in a distributed file system.
- ISO 20022
- ISO 20022 is a universal financial industry message scheme supported by ISO, the International Standards Organization. ISO 20022 is a methodology for creating financial messaging standards.
It covers five financial business domains:
- Payments — message supporting cash account management, payments initiation, clearing and settlement, and cash management.
- Cards — messages supporting card transactions between acceptor and acquirer; acquirer and issues; sales system and POI; terminal management; clearing, settlement, fee collection and other messages.
- Securities — Messages supporting pre-trade, trade, post-trade, clearing and settlement, securities management, securities account management, reconciliation, asset servicing, collateral management, etc.
- Trade Services — Messages supporting procurement, trade finance products and services, forecasting, reconciliation, accounting, remittance information, etc.
- FX — Messages supporting pre-trade, trade, post-trade, notification, clearing and settlement, reporting and reconciliation of FX products.
J
K
- Know Your Customer (KYC)
- Know your customer (know your client) is the process of a business verifying the identity of its clients and assessing potential risks of illegal transactions for the business relationship. The term refers to the bank regulations and anti-money laundering regulations that govern these activities. Know your customer processes are employed by companies of all sizes for the purpose of ensuring their proposed agents, consultants, or distributors are anti-bribery compliant. Banks, insurers and export creditors are increasingly demanding that customers provide detailed anti-corruption due diligence information as part of their risk management processes.
L
- Lambo
- A Lambroghini. When a HODL-er will cash out of cryptocurrency and buy a Lambo (Lambroghini). As in "When Lambo? When ETH hits $5K."
- Layer 2
- Projects built on top of existing cryptocurrencies that allow for greater volumes of transactions to be processed without using energy-intense Proof of Work (PoW) mining techniques.
- Ledger
- A collection of transactions recorded chronologically.
- Lightweight Node
- A blockchain node that does not need to store a full copy of the blockchain and often passes its data to full nodes to be processed. Lightweight nodes are found on mobile devices and other devices without the computing power to handle the full set of blockchain tasks. Lightweight nodes are generally found on smart phones and Internet of Things (IoT) devices—devices with limited computational and/or storage capability.
- Linket
- A linket is a label for a deep link. See Deep Link.
M
- M of N
- A multi-signature operation that requires keys from M out of N verifiers to authorize a transaction. See Multisig.
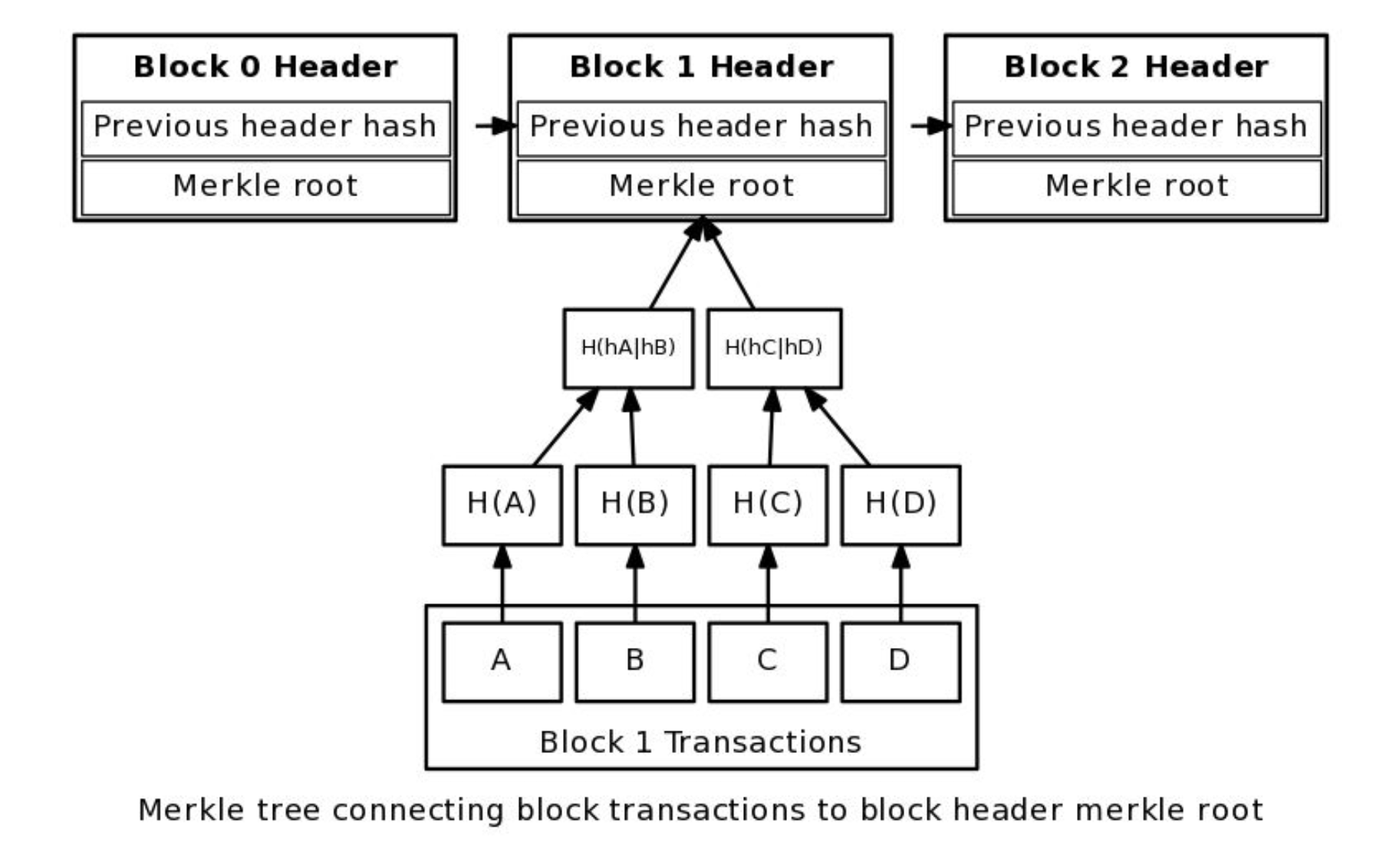
- Merkle Tree
- A data structure where the data is hashed and combined until there is a singular root hash that represents the entire structure.
- Miners
- The individuals that add new blocks to public blockchains that use proof of work, such as Bitcoin or Ether. Their actions both secure the entries on a public blockchain, and provide a mechanism for the distribution of new coins. They gain the right to add new blocks by spending computational resources, and the network rewards miners by allocating new coins to them.
- Mining
- The act of performing the required work (as defined by the system's consensus algorithm) to add the next block to the system and usually rewarded with a cryptocurrency.
- Mining Rigs
- A complete bitcoin-mining data center hardware platform. Each ASIC has more than 100 cores, all of which operate independently to run Bitcoin’s SHA-256 hashing algorithm. A control board on the top of the machine coordinates the work, downloading the block header to be hashed and distributing the problem to all the hashing engines, which then report back with solutions and the random numbers they used to get them. The standard algorithm takes 64 steps to complete, but in Bitcoin it is run twice for each block header, meaning a full round requires 128 steps that are heavy on integer addition.
- Mobile Wallet
- Mobile wallets are cryptocurrency wallets designed for use on mobile devices.
- Multichain
- MultiChain is an off-the-shelf platform for the creation and deployment of private blockchains, either within or between organizations. It aims to overcome a key obstacle to the deployment of blockchain technology in the institutional financial sector, by providing the privacy and control required in an easy-to-use package. Like the Bitcoin Core software from which it is derived, MultiChain supports Windows, Linux and Mac servers and provides a simple API and command line interface.
- Multi Signature Wallet
- Multi Signature Wallets (Multisig) provide enhanced security by requiring that multiple keys are used to authorize a transaction, reducing the risk of theft if a single private key is compromised.
Multisig is also used as a simple smart contract within the Bitcoin ecosystem. A multisig address is generated with multiple public keys and a specification of how many of those keys must sign to release the funds. These "contracts" use M of N multisig addresses to execute. For example, three public keys are used to create the payment address (the buyer's, seller's, and arbitrator's), and the transaction must be signed by two parties for the funds to be released. A typical trade takes place when the buyer and seller sign the transaction to release the funds to the appropriate party. But in case of a dispute, the arbitrator will side with either the buyer or seller, and these two parties' keys will release the funds to the appropriate party.
N
- Native Digital Asset
- Tokens and cryptocurrency specific to a particular blockchain. The native digital asset on the Bitcoin blockchain is bitcoin (BTC). The native digital asset of the Ethereum blockchain is ether (ETH).
- Node
- An individual system within the blockchain.
- Nonce
- A nonce is an arbitrary number,usually randomly selected, that can only be used once. It is similar in spirit to a nonce word, a word coined for one single occasion only, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused in replay attacks.
- Nostro Account
- Nostro account refers to an account that a bank holds in a foreign currency in another bank. Nostros, a term derived from the Latin word for "ours," are frequently used to facilitate foreign exchange and trade transactions. Nostro accounts have been used as early prototypes for evaluating blockchain for interbank transfers and to assess the utility of blockchain in the financial services industry.
O
- Off Chain
- Off chain refers to data and processes executed off the blockchain in centralized or legacy systems.
- Online Wallet
- Online wallets store cryptocurrency and identification in the cloud. Online wallets are hot wallets that are always connected to the internet and can be accessed via different internet browsers such as Google Chrome, Apple's Safari, Mozilla's Firefox, or Microsoft's Internet Explorer (IE).
- Open data
- Publicly available data that are made available consistent with relevant privacy, confidentiality, security, and other valid access, use, and dissemination restrictions, and are structured in a way that enables the data to be fully discoverable and usable by end users. Generally, open data are consistent with principles of such data being public, accessible, machine-readable, described, reusable, complete, timely, and managed post-release. The data on permissionless blockchains is open data because anyone can explore the content of the blocks.
- Oracle
- Oracles provide the connection between real world events and the blockchain. Oracles provide the necessary data to trigger smart contracts to execute when the terms of the contract are met. These conditions could be anything associated with the smart contract — temperature, passage of time, payment completion, price changes, rates of exchange. Oracles are the way for smart contracts to interact with data outside of the blockchain environment. An oracle entity records data about real-world events such as completion of a delivery, the ambient temperature measured on an IoT sensor, or the outcome of a title search and triggers the appropriate smart contract action. Oracles serve as a reference for smart contracts.
P
- Permissioned Blockchain
- A system where every user must have their permissions assigned by an administrator. Permissioned blockchain applications are more suited to regulated industries or in business processes that require confidentiality of some or all of its transactions.
- Permissionless Blockchain
- A system where all users' permissions are equal and not set by any administrator.
- Protected Health Information (PHI)
- Protected Health Information is individually identifiable health information that is created, received, or maintained by a covered entity with responsibility to protect it — doctors, hospitals, health insurance firms, pharmacies, etc.
- Personally identifiable information (PII)
- Information that can be used to distinguish or trace an individual's identity, either alone or when combined with other information that is linked or linkable to a specific individual.
- Pluggable Consensus
- Pluggable consensus uses pluggable notaries which are services that provide transaction ordering and timestamping. Notaries are composed of multiple mutually distrusting parties who use a standard consensus algorithm. A notary is responsible for validating transactions. Every state has an appointed notary.
- PoET Consensus
- Proof of Elapsed Time (PoET) is a consensus mechanism algorithm that is used on permissioned blockchain networks to decide the mining rights or the block winners on the network. Permissioned blockchain networks require any prospective participant to identify themselves before they are allowed to join. Based on the principle of a fair lottery system where every single node is equally likely to be a winner, the PoET mechanism spreads the chances of a winning fairly across the largest possible number of network participants.
Each participating node in the network is required to wait for a randomly chosen time period, and the first one to complete the designated waiting time wins the new block. Each node in the blockchain network generates a random wait time and goes to sleep for that specified duration. The one to wake up first, the one with the shortest wait time, wakes up and commits a new block to the blockchain, broadcasting the necessary information to the whole peer network The same process then repeats for the discovery of the next block. The PoET network consensus mechanism needs to ensure two important factors. First, that the participating nodes genuinely select a time that is indeed random and not a shorter duration chosen purposely by the participants in order to win, and two, the winner has indeed completed the waiting time. - Proof of Authority (PoA) Consensus
- Proof of Authority is a modified form of Proof of Stake (PoS) where instead of stake, holding coins with a monetary value, a validator’s identity performs the role of stake. Identity means the correspondence between a validator’s personal identification on the platform with officially issued documentation for the same person, i.e. certainty that a validator is exactly who that person represents to be. Proof of Authority enables designated individuals or organizations to validate transactions that are added to the blockchain or distributed ledger.
- Proof of Existence
- Proof of Existence is a service that allows one to anonymously and securely store online proof of existence of any document. This service simply stores the cryptographic digest of the file, linked to the time that a user submits his/her document. The cryptographic digest or fingerprint- not the actual document is stored in blockchain. This maintains the privacy of the document. Users store the signature and timestamp associated with a legal document in the blockchain and validate it anytime using native blockchain mechanisms.
- Proof of Stake (PoS) Consensus
- A consensus model where the blockchain network is secured by users locking an amount of cryptocurrency into the blockchain system, a process called staking. They have a stake in the coin. PoS distributes coins to people who are able to prove ownership of existing coins. They have a stake in the coin. Participants with more stake in the system are more likely to want it to succeed and to not be subverted, which gives them more weight during consensus.
- Proof of Work (PoW) Consensus
- Proof of Work is a competitive consensus algorithm. Each node races to solve a difficult puzzle first. Doing so earns the right to produce a block and to a cryptocurrency reward, a new coin. A consensus model where a mining node obtains the right to publish the next block by expending time, energy, and computational cycles to solve a hard-to-solve, but easy-to-verify problem (e.g., finding the nonce which, when combined with the data to be added to the block, will result in a specific output pattern). See mining.
- Protocol
- A blockchain protocol is a set of rules that dictate how the computers in the network, called nodes, should verify new transactions and add them to the database. The protocol employs cryptography, game theory, and economics to create incentives for the nodes to work toward securing the network instead of attacking it for personal gain. If set up correctly, this system can make it extremely difficult and expensive to add false transactions but relatively easy to verify valid ones.
- Provenance
- A record of ownership of a work of art or an antique, used as a guide to authenticity or quality. Provenance blockchain applications track the end-to-end supply chain of a wide of products including diamonds, precious metals, wine, watches and high value or high risk foodstuffs like fish, coffee and vegetables.
- Public Key Encryption
- Public/Private Key Cryptography
- A cryptographic system where users have a private key that is kept secret and used to generate a public key (which is freely provided to others). Users can digitally sign data with their private key, and the resulting signature can be verified by anyone using the corresponding public key. Also known as asymmetric cryptography.
Q
- Quorum
- JPM Chase's enterprise-ready distributed ledger and smart contract platform. Quorum™ is an enterprise-focused version of Ethereum.
R
- R3 Corda Alliance
- Rent Seeking
- Rent seeking is an individual's or entity's use of company, organizational or individual resources to obtain economic gain without reciprocating any benefits to society through wealth creation. Rent seeking is trying to use protective regulations or "rights" to derive income without adding anything to the economic activity. In the blockchain ecosphere, distributed applications (dApps) on the blockchain and cryptocurrency seek to remove rent seeking intermediaries (like centralized banks for currency exchange or social media companies who hold and sell your personal data) to enable individuals to have more control over their economic activities.
- Resilience
- The ability to prepare for and adapt to changing conditions and withstand and recover rapidly from disruption. Resilience includes the ability to withstand and recover from deliberate attacks, accidents, or naturally occurring threats or incidents.
- Ricardian Contract
- Blockchain-based smart contracts that incorporate legal prose are Ricardian contracts. Ricardian contracts are human-readable legal agreements that once agreed upon and signed by both parties, get converted into machine readable smart contract code that reflect the inventions of both parties.
A Ricardian contract places the defining elements of a legal agreement in a format that can be expressed and executed in software. A Ricardian contract can be defined as a single document that is a) a contract offered by an issuer to holders, b) for a valuable right held by holders, and managed by the issuer, c) easily readable (like a contract on paper), d) readable by programs (parsable like a database), e) digitally signed, f) carrying the keys and server information, and g) allied with a unique and secure identifier. - Risk
- A measure of the extent to which an entity is threatened by a potential circumstance or event, and typically is a function of the adverse impact, or magnitude of harm, that would arise if the circumstance or event occurs; and the likelihood of occurrence.
- Risk management
- The program and supporting processes to manage risk to operations (including mission, functions, image, reputation), assets, individuals, other organizations, and the Nation, and includes: establishing the context for risk-related activities; assessing risk; responding to risk once determined; and monitoring risk over time.
- Risk management strategy
- The description of how entities intend to assess risk, respond to risk, and monitor risk, making explicit and transparent the risk perceptions that organizations routinely use in making both investment and operational decisions.
- Risk response
- Accepting, avoiding, mitigating, sharing, or transferring risk to operations, assets, individuals, other organizations, or the Nation.
- Round Robin Consensus Model
- A consensus model for private blockchains where nodes are pseudo randomly selected to create blocks, but a node must wait several block creation cycles before being chosen again to add another new block. This model ensures that no one participant creates the majority of the blocks, and it benefits from a straightforward approach, lacking cryptographic puzzles, and having low electric power requirements.
S
- Safe Agreement for Future Tokens (SAFT)
- A SAFT acts as a forward contract for tokens, with the contract converting upon deployment of a functioning network. Accredited investors buy tokens via cryptocurrency purchase agreements. Startups usimg SAFTs aren't selling equity stakes, but the rights to some of the tokens used as part of its network. A conversion that might happen years after the initial token sale.
- Scalability
- Security Token Offering (STO)
- Security Coin Offerings are regulated versions of Initial Coin Offerings. These coins are investments in the firm issuing the coin. Unlike an ICO, there is no need to define a specific business use for the coin. STO investors have legal rights such as voting or revenue distribution rights. All tokens are backed up by particular assets such as equity in a start up or securitized debt instruments. STOs are registered through financial authorities. At present, STO tokens are not supported by exchanges. (Also Secure Coin Offerings - SCO)
- Seed Generator
- A mnemonic phrase, mnemonic recovery phrase or mnemonic seed is a list of words which store all the information needed to recover a cryptocurrency wallet. Wallet software will typically generate a mnemonic backup phrase and instruct the user to write it down on paper. If the user's computer breaks or their hard drive becomes corrupted, they can download the same wallet software again and use the paper backup to get their cryptocurrency back. Anyone who discovers or figures out the phrase can steal the associated cryptocurrency. Seeds should be treated like passwords and not be easy to decipher.
- Self-Sovereign Identity
- Self-sovereign identity is a concept where an individual is able to control his/her identity attributes and their personal data without the requirement of a central authority (government, bank, etc.) issuing documents or other objects used to prove your identity. Self-sovereign identity is a digital record or container of identity transactions that you control. You can add more data to it yourself, or ask others to do so. Self-sovereign identity is viewed as the identity layer of the internet. The Sovrin Foundation and uPort are two self-sovereign identity projects.
- Segregated Ledgers
- Segregated ledgers are confidentiality solutions that use encryption to create what we refer to as "logically segregated" ledgers. Transaction data is still replicated to all participants, but only those who are entitled to view the data can decrypt it.
- Shoal
- Collections of such IoT devices may be organized into enclaves, groups or "shoals" that operate as autonomous or semi-autonomous groups of devices functioning as a collective having a common objective or mission.
- Sharding
- Sharding is a concept that is widely used in databases to make them more efficient. A shard is a horizontal portion of a database with each shard stored in a separate server instance. This spreads the load and makes the database more efficient. In blockchain each node will have only a part of the data on the blockchain not the entire content of the blockchain when sharding is implemented. Nodes that maintain a shard maintain information only on that shard in a shared manner so within a shard the decentralization is still maintained. Each node doesn't load the information on the entire blockchain helping with performance and scalability. Blockchains that implement sharding use proof of stake (PoS) consensus algorithm.
- Side Chains
- SIM Hijacking | SIM Swappers
- A type of cyber crime where criminals trick a cellphone provider to transfer their target's telephone number to a SIM card they control. SIM Swapping refers to a scam in which a thief asks a wireless carrier to redirect a victim's phone number to a SIM card contained within a phone owned by the thief. Once the phone number has been ported to the thief's phone, the thief can then receive or place calls using the stolen number and purporting to be the victim. The thief may also exploit text-based two-factor authentication in order to reset passwords or otherwise intercept text messages containing security codes needed to access the victim's bank or cryptocurrency accounts.
- Smart Contract
- Smart contracts are programs deployed and executed on a blockchain that deliver autonomous or semi-autonomous transactions between parties. Smart contracts can express triggers, conditions, and business logic to enable a more complex programmable transactions similar to scripts in traditional databases. Smart contracts are modular, repeatable, autonomous scripts, that are used to build applications. Smart contracts can be coded to reflect any data-driven business or engineering logic. Relationships and obligations defined in smart contracts benefit from blockchain security logic and the increase in verifiability that blockchain networks provide. Smart contracts operate in the exact same manner for all participants in a particular transaction or blockchain-based application. Smart contracts can be used to automate the movement of cryptocurrency according to prescribed rules and conditions.
- Soft Fork
- A fork that will not completely prevent users who do not adopt it from using the changed blockchain system. A soft fork can be backwards compatible, only requiring that a majority of mining nodes upgrade to enforce the new soft fork rules.
- Software-Defined Machine
- Software-defined machine (SDM) architecture provides a standard way for developers to abstract the machine software (including machine apps) from the underlying hardware and run parts of it on secure virtual machines.
- Software Wallet
- Software Wallets are downloaded applications maintained on a desktop or mobile device that allow storage of private keys securely on the device.
- Solid
- Entity system designed by Tim Berners-Lee
- Solidity
- Solidity is a contract-oriented, high-level language for implementing smart contracts. It was influenced by C++, Python and Java Script and is designed to work with the Ethereum Virtual Machine (EVM).
- Simplified Payment Verification (SPV)
- Simple Payment Verification (SPV) is a technique described in Satoshi Nakamoto's paper. SPV allows a lightweight client to verify that a transaction is included in the Bitcoin blockchain, without downloading the entire blockchain.
- Simplified Payment Verification (SPV) Wallet
- SPV Wallets performs two functions: a) it ensures that a user's transactions are in a block, and b) it provides confirmations that additional blocks are being added to the chain. An SPV wallet listens for incoming transactions to a user's cryptocurrency addresses.
- Spending Tokens
- Spending tokens is exchanging tokens by moving tokens between wallets in exchange for something of value. After a token is "spent" it still exists. In contrast, burning tokens refers to using tokens to acquire something of value. At the end of the transaction the token is destroyed.
- Stablecoin
- Coins designed to be less volatile than traditional cryptocurrency coins. Stablecoins are pegged to a fiat currency like the dollar or the euro.
- Stake
- Stake refers to entities holding cryptocurrnecy coins with a monetary value for the purpose of participating in consensus decisions on a blockchain. Stake is an amount of cryptocurrency that the user has invested into the system, either by locking it via a special transaction type, or by sending it to a specific address; the amount of staked cryptocurrency is generally no longer able to be spent. The likelihood of a user creating a new block is tied to the ratio of their stake to the overall blockchain system amount of staked cryptocurrency. The value of the stake is used in some consensus algorithms to determine which entity gets to execute the consensus algorithm and add new blocks to the blockchain. (See Proof of Stake (PoS) Consensus
- Subledger
- Supply chain
- A linked set of resources and processes between multiple tiers of entities that begin with the sourcing of products and services and extends through the design, development, manufacturing, processing, handling, and delivery of products and services to the acquirer.
- Supply chain risk
- Risks that arise from the loss of confidentiality, integrity, or availability of information or information systems and reflect the potential adverse impacts to organizational operations (including mission, functions, image, or reputation), organizational assets, individuals, other organizations, and the Nation.
- Supply chain risk management
- The process of identifying, assessing, and mitigating the risks associated with the global and distributed nature of products and service supply chains.
- Sybil Attack
- A Sybil attack is a type of security threat when a node in a network claims multiple identities. Sybils are just copies of nodes that a malicious adversary can create to look like there are a lot of different participants, when in fact all those pseudo‐participants are really controlled by the same adversary. Most networks, like a peer-to-peer network, rely on assumptions of identity, where each computer represents one identity. It is named after the subject of the book Sybil, a case study of a woman diagnosed with dissociative identity disorder.
T
- Tangle
- A blockchain technology focused on Industrial Internet of Things (IIoT), Edge Computing, and sensors. Tangle is a transactional settlement and data transfer layer for the Internet of Things. It is based on a new distributed ledger, the Tangle, which claims to overcome the inefficiencies of current Blockchain designs and introduces a new way of reaching consensus in a decentralized peer-to-peer system.
- Threat
- Any circumstance or event with the potential to adversely impact organizational operations (including mission, functions, image, or reputation), organizational assets, individuals, other organizations, or the Nation through an information system via unauthorized access, destruction, disclosure, modification of information, and/or denial of service.
- Threat Source
- The intent and method targeted at the intentional exploitation of a vulnerability or a situation and method that may accidentally trigger a vulnerability. Synonymous with threat agent.
- Tokenization
- The representation of rights or assets in distributed ledger units (DLUs)
- Transaction
- A recording of a transfer of assets (digital currency, units of inventory, etc.) between parties.
- Transaction Pool
- A distributed queue where candidate transactions wait until they are added to the blockchain. Also known as Unspent Transaction Pool.
- Trustworthy information system
- An information system that is believed to be capable of operating within defined levels of risk despite the environmental disruptions, human errors, structural failures, and purposeful attacks that are expected to occur in its environment of operation.
- Turing Complete
- A system (computer system, programming language, etc.) that can be used for any algorithm, regardless of complexity, to find a solution. A full node in a blockchain is Turing complete.
- Turing Test
- Developed by Alan Turing in 1950, a Turing test says that if a computer or machine exhibits behavior indistinguishable to humans from that of a person, then it demonstrates intelligent behavior.
- Two Factor Authentication (2FA)
- Two Factor Authentication, also known as 2FA, two step verification or TFA (as an acronym), is an extra layer of security that is known as "multi factor authentication" that requires not only a password and user name but also something that only, and only, that user has on them, i.e. a piece of information only they should know or have immediately to hand - such as a physical token. 2FA was originally created for use outside of cryptocurrency, and has recently been adopted by cryptocurrency services.
U
- uPort
- A self-sovereign identity system on Ethereum spun out by Consensys.
- Utility Token
- Unspent Transaction Output (UTXO)
- UTXO is an acronym for "Unspent Transaction Output." Unspent transaction outputs are important because fully validating nodes use them to figure out whether or not transactions are valid. All inputs to a transaction must be in the UTXO database for it to be valid. If an input is not in the UTXO database, the transaction is either attempting a double-spend of coins that were already spent; or the transaction is trying to spend coins that do not exist. For Bitcoin one UTXO is one coin.
V
- Verifier
- A verifier is a third party trusted to provide some types of information about the external world. When validation of a transaction depends on an external state, the verifier is requested to check the external state and to provide the result to the validator (miner) which then validates the condition. A verifier can be implemented as a server outside the blockchain and has the permission to sign transactions using their own key pair to digitally sign a transaction. For example, a verifier may validate the characteristics of a physical asset like a diamond that is tokenized on the blockchain. A Bitcoin oracle is an instance of a verifier.
- Vulnerability
- Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source.
- Vulnerability Assessment
- Formal description and evaluation of the vulnerabilities in an information system.
W
- Wallet
- Software used to manage public/private keys and addresses used for transactions using cryptocurrency or blockchain tokens. The blockchain contains a series of digital "wallets" that have a unique identifier and show the flow of money into and out of the wallet.
X
Y
Z
- zCash
- zCash is a cryptocurrency aimed at using cryptography to provide enhanced privacy for its users compared to other cryptocurrencies such as Bitcoin.
- Zero Knowledge Proof (ZKP)
- In zero knowledge proof systems the transaction contains a proof of its validity without containing any of the confidential data itself, which can be revealed separately. Zero Knowledge confirmation (confirmation without information in public blockchain) might solve confidentiality issues, but it is still being developed. ZKP consensus is desirable because it is believed to be much more energy-intensive than even PoW.
- zk-snark — Zero-Knowledge Succinct Non-Interactive Argument of Knowledge
- zk-snarks, Zero-Knowledge Succinct Non-Interactive Argument of Knowledge, is a variant of zero-knowledge proofs not requiring interaction between prover and verifier. It allows verification of the correctness computations without having to execute them, without learning what was executing, just that it was done correctly. It can potentially help ethereum scale up to 500 transactions per second. JPMorgan added zk-snarks technology developed by the startup behind zcash to Quorum, the bank's ethereum-based private blockchain.
